Why is Industrial OT Security Different from IT Security?
Whilst in IT the primary goal of security is to protect the confidentiality of data, in OT (Operational Technology) the focus shifts to ensuring that industrial systems and processes are safe, available, and reliable. Systems can be taken offline entirely, grinding operations to a halt and if tampered with unexpectedly, safety can be compromised causing injuries. It quickly becomes clear that, although the threats may remain the same, the risks and impact can be much more severe.
- Legacy Systems: Many OT systems run on outdated software, making them vulnerable to modern threats.
- Safety-Critical Operations: Breaches can disrupt essential services, risking safety and financial loss.
- Integration Challenges: Convergence with IT systems introduces additional complexity.
Challenges
What are the security challenges impacting Industrial OT?
OT systems are critical to your organisation and require the right level of protection.
Even though cyber-attacks on operational technology are more complex and prevalent than ever before, many organisations do not have a comprehensive inventory of industrial devices they need to protect. Here are some of the main challenges an OT team may face:
Solutions
Our Industrial OT Security Solutions and Managed Services
We offer OT managed services to ensure you have protection throughout your industrial network to guard you against known threats and zero-day attacks, so you can keep your operations running safely and without disruption.
Whether you need enhanced Industrial Control System (ICS) /OT visibility, want to implement zero trust principles, or are seeking a converged IT/OT security strategy, we can help.
Request your assessment
Your technology partner
Why Choose Us As Your Industrial OT Security Managed Services Partner?
Our OT Managed Services provide real-time, ITIL-based management and delivery, ensuring seamless operations and robust security tailored to the unique demands of industrial environments.
With our flexible subscription model, you maximise the critical OT security technologies that keep your business running—only paying for what you need.
Extend Your Protection with Additional Managed Services
You can enhance your OT Managed Service with additional layers of security and monitoring—or purchase them as standalone managed services:
| OT Detection and Response Service | OT SOC Lite Services | OT Cyber Security Strategy Service Review |
|---|---|---|
| Proactively monitor your OT environment, detect anomalies, and respond to potential threats to minimise downtime and mitigate risks. | Gain 24/7 support from a Security Operations Centre (SOC) designed specifically for OT environments. Our expert team provides threat detection, incident management, and guidance to safeguard your operations. | Assess and refine your OT cyber security strategy to identify gaps, adapt to emerging threats, and maintain compliance. This ensures your security approach remains effective and future-proof. |
Here’s why we’re the trusted choice for securing and managing critical infrastructure:
With over three decades of experience in IT and OT security, we understand the nuances of protecting systems that manage physical processes. From industrial control systems to critical infrastructure, we have the expertise to address vulnerabilities in legacy systems and complex, converged IT-OT environments.
We use proven frameworks and adhere to strict regulations to deliver customised solutions that integrate seamlessly into your existing operations. Whether you’re a manufacturer, utility provider, or healthcare organisation, we adapt our strategies to fit your industry and specific operational requirements and regulations.
Operational technology requires constant uptime. Our managed services operate 24/7, ensuring rapid incident response and ongoing monitoring to keep your systems secure and operational.
IDS-INDATA is certified to the highest industry standards, including ISO 27001, IEC 62443, Cyber Essentials, and the NIST (including NIS2), ensuring that your OT security strategy aligns with best practices. We combine this with a commitment to continuous improvement, keeping up defences for global companies such as Siemens ahead of evolving threats.
Innovation is at the heart of what we do. We stay at the forefront of OT security trends, employing cutting-edge technologies like industrial IoT (IIoT) integration and advanced analytics to protect your systems against emerging risks.
Our goal is not just to deliver technology but to ensure measurable results. Whether reducing downtime, enhancing compliance, or preventing costly breaches, we align every solution and service with your operational and strategic goals.
With a 99% customer renewal rate, we’ve built long-term relationships across industries. Our clients value our ability to balance technical excellence with practical, actionable strategies.
Protect your operational technology with a partner you can trust. Contact IDS-INDATA today to learn how we can secure your critical infrastructure and ensure uninterrupted operations.
Our Approach
Our Approach To Industrial OT Cyber Security Solutions
We take a structured, methodical approach to securing your Operational Technology (OT) environments. Our process is designed to address unique challenges, minimise risks, and enhance the resilience of critical systems.
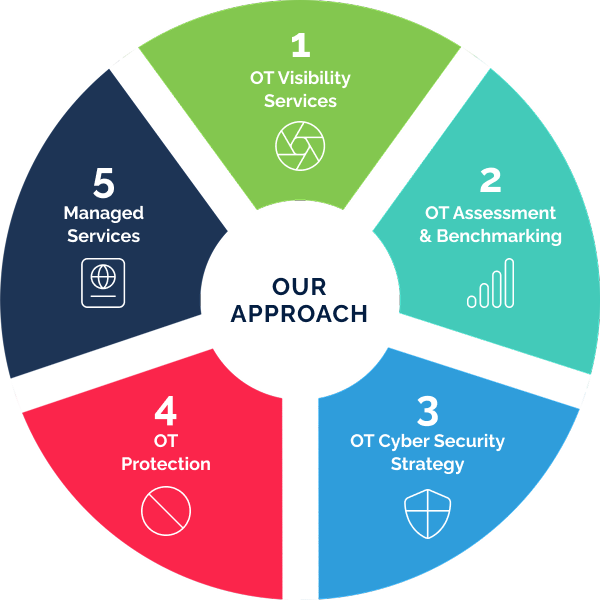
1. OT Visibility Services (Assessment)
- Identifying and modelling OT assets, zones, and conduits.
- Detecting vulnerabilities within the OT environment.
- Analysing IT/OT traffic flows to understand dependencies.
KEY OUTCOMES
- Full visibility into OT assets, zones, and conduits.
- Early identification of vulnerabilities and risks.
- Improved understanding of IT/OT traffic dependencies for proactive security.
2. OT Assessment and Benchmarking (Design)
- Evaluating the current state of OT security to identify gaps.
- Developing a roadmap for addressing risks and improving resilience.
- Benchmarking against industry standards and assessing vulnerability criticality.
KEY OUTCOMES
- A detailed assessment of gaps and vulnerabilities.
- A clear roadmap for enhancing OT security.
- Prioritised vulnerabilities, ensuring effective resource allocation.
3. OT Cyber Security Strategy
- Establishing an OT cybersecurity policy with risk mitigation and threat modelling.
- Addressing compliance requirements and creating an incident response plan.
- Conducting security awareness training to embed a security-first culture.
KEY OUTCOMES
- A comprehensive cybersecurity policy tailored to your organisation.
- Improved compliance with regulatory and industry standards.
- A practical incident response plan ready for execution.
- Enhanced governance and team-wide security awareness.
4. OT Protection (Implementation)
- Implementing OT network segmentation to reduce attack surfaces.
- Enabling secure remote access for controlled connectivity.
- Offering managed services to ensure continuous OT system protection.
KEY OUTCOMES
- Reduced attack surface through segmented networks.
- Secure and controlled access to OT environments.
- Continuous monitoring and protection with managed services.
5. OT Security Managed Service
- Ensuring continuous security monitoring and proactive threat detection in OT environments.
- Providing real-time incident response to mitigate cyber threats before they escalate.
- Leveraging Security Operations Centre (SOC) services for ongoing visibility and risk management.
KEY OUTCOMES
- 24/7 monitoring for early threat detection and response.
- Minimised downtime through rapid incident containment and mitigation.
- Enhanced operational resilience with continuous security oversight.
At IDS-INDATA, our approach ensures your industrial OT environment is not only secure but also optimised for operational excellence. By combining expertise, innovation, and a commitment to your success, we protect your systems while enabling you to focus on what you do best. Don’t just take it from us – hear what our customers have to say:
Get in touch
Contact us
Ready to secure your OT environment? Contact us to discuss how our approach can safeguard your operations.

